FUD Crypter Tutorial
WHAT IS CRYPTORS???
As said above, Crypter is hacking program or application used to hide our viruses, RATs or any keylogger from antiviruses so that they are not detected and deleted by antiviruses. Thus, a crypter is a program that allow users to crypt the source code of their program. Generally, antivirus work by splitting source code of application and then search for certain string within source code.
If AV detects any certain malicious strings, it either stops scan or deletes the file as virus.
What does Crypter do???
Crypter simply assigns hidden values to each individual code within source code. Thus, the source code becomes hidden. Hence, our sent crypted trojan and virus bypass antivirus detection and our purpose of hacking them is fulfilled without any AV hindrance. Not only does this crypter hide source code, it will unpack the encryption once the program is executed.
What is FUD ???
FUD is acronym for Fully UnDetectable. With increased use of Crypters to bypass antiviruses, AV became more advanced and started including crypter definitions to even detect crypter strings within code. So, use of crypter to hide Ardamax keylogger and RATs became more complicated as nowadays, no publicly available crypter is FUD.
So, if you crypt RATs with publicly available crypters, they are bound to be detected by antiviruses. This is because most FUD crypters remain “FUD” for maximum of one or two days after their public release. To obtain FUD crypters, you have to either search for it in hacking forums or make one (which is somewhat tedius.. I am working on this).
How do I get one Crypter???
There are many crypters out on web. But, most of them are not FUD. So, as stated above, either you have to search for one FUD crypter or make one
If AV detects any certain malicious strings, it either stops scan or deletes the file as virus.
What does Crypter do???
Crypter simply assigns hidden values to each individual code within source code. Thus, the source code becomes hidden. Hence, our sent crypted trojan and virus bypass antivirus detection and our purpose of hacking them is fulfilled without any AV hindrance. Not only does this crypter hide source code, it will unpack the encryption once the program is executed.
What is FUD ???
FUD is acronym for Fully UnDetectable. With increased use of Crypters to bypass antiviruses, AV became more advanced and started including crypter definitions to even detect crypter strings within code. So, use of crypter to hide Ardamax keylogger and RATs became more complicated as nowadays, no publicly available crypter is FUD.
So, if you crypt RATs with publicly available crypters, they are bound to be detected by antiviruses. This is because most FUD crypters remain “FUD” for maximum of one or two days after their public release. To obtain FUD crypters, you have to either search for it in hacking forums or make one (which is somewhat tedius.. I am working on this).
How do I get one Crypter???
There are many crypters out on web. But, most of them are not FUD. So, as stated above, either you have to search for one FUD crypter or make one
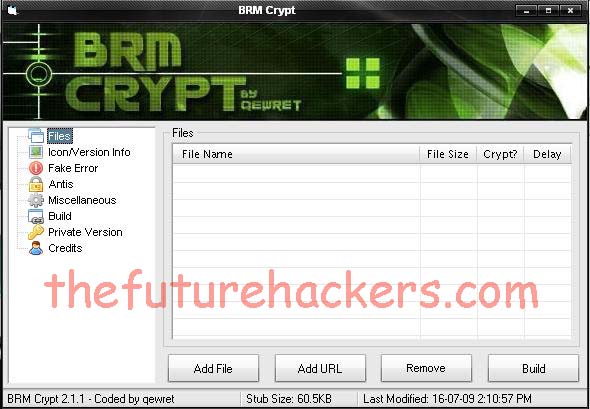
Screen shot of a crypter:
Crypters may be coded in different launguages but there functionality remain almost the same i.e to crypt your detectable servers so they become FUD...
FUD(FULLY UNDTECTABLE)
UD=UNDETECTABLE
A FUD crypter is theoretically/practically not detected by any antiviruses at the time of it being scanned on Virus Scanners.
Screen shot of a FUD scan:
UD=UNDETECTABLE
A FUD crypter is theoretically/practically not detected by any antiviruses at the time of it being scanned on Virus Scanners.
Screen shot of a FUD scan:
With increased use of Crypters to bypass anti-viruses, AntiV iruses became more advanced and started including crypter definitions to even detect crypter strings within code. So, use of crypter to hide Rats(PI, Bifrost), Stealers and Bots became more complicated as nowadays, no publicly available crypter is FUD.
So, if you crypt RAT, Bot servers with publicly available crypters, they are bound to be detected by antiviruses. This is because most FUD crypters remain "FUD" for maximum of one or two days after their public release.Then they become UD.
So, if you want a FUD or close to FUD crypter, I suggest Buying one or learn to make public crypters FUD or Semi-FUD(The crypter which is detected by 2-3 AV's).
So, if you crypt RAT, Bot servers with publicly available crypters, they are bound to be detected by antiviruses. This is because most FUD crypters remain "FUD" for maximum of one or two days after their public release.Then they become UD.
So, if you want a FUD or close to FUD crypter, I suggest Buying one or learn to make public crypters FUD or Semi-FUD(The crypter which is detected by 2-3 AV's).
Parts of a Crypter
A Crypter has 2 parts:
* Client
* Stub
A) The client is the interface where we may upload our file and use the options it brings, according to the programmer that made the crypter and crypt our files.
B) The stub is an executable file(.exe) or a. Dll some times. This file is used as a filter for files that are uploaded to the client crypter.
Functioning :
Once the client is open, it loads its stub ... goes through the file, and accordingly the file gets crypted as the stub.
Here is how executable crypters work:
1) The actual processor commands of a protected binary are crypted/obscured/munged whatever
2) When the protected application first starts, a small decrypter stub is first run that restores all of the original processor commands for the executable in memory.
3) Finally, the decrypter stub ends and transfers execution to the original entry point (OEP) and the program runs normally. So, basically the crypter's that have in-built stubs gets detected very fast, the others take some time to get detected.
Also you can modify the stub once it gets detected by changing the entry and exit points.
A Crypter has 2 parts:
* Client
* Stub
A) The client is the interface where we may upload our file and use the options it brings, according to the programmer that made the crypter and crypt our files.
B) The stub is an executable file(.exe) or a. Dll some times. This file is used as a filter for files that are uploaded to the client crypter.
Functioning :
Once the client is open, it loads its stub ... goes through the file, and accordingly the file gets crypted as the stub.
Here is how executable crypters work:
1) The actual processor commands of a protected binary are crypted/obscured/munged whatever
2) When the protected application first starts, a small decrypter stub is first run that restores all of the original processor commands for the executable in memory.
3) Finally, the decrypter stub ends and transfers execution to the original entry point (OEP) and the program runs normally. So, basically the crypter's that have in-built stubs gets detected very fast, the others take some time to get detected.
Also you can modify the stub once it gets detected by changing the entry and exit points.
Types of Crypter
* External Stub
* Internal Stub
* Runtime
* ScantimeExternal Stub : Well most of you have downloaded a public crypter by now and when you open the folder you have seen 2 things:
Client.exe and Stub.exe
These type of crypters are called External Crypter in which the functionality of the crypter pretty much depends on the external stub.
You delete the stub and the crypter is useless.
Internal Stub : The crypters that contain only Client.exe fall under this category. In this the stub is coded within the crypter.
There are ways to detach the stub from the crypter, but in some other tutorial.
Runtime Crypters : The crypters that crypts a server that remains Undetectable upon running in the memory of a PC is called a runtime crypter.
This is the one you want for all your servers and executables.
Scantime Crypter : The crypters that crypts a server that remains Undetectable upon scanning by AntiViruses but when run in the PC gets detected by the AntiVirus.
* External Stub
* Internal Stub
* Runtime
* ScantimeExternal Stub : Well most of you have downloaded a public crypter by now and when you open the folder you have seen 2 things:
Client.exe and Stub.exe
These type of crypters are called External Crypter in which the functionality of the crypter pretty much depends on the external stub.
You delete the stub and the crypter is useless.
Internal Stub : The crypters that contain only Client.exe fall under this category. In this the stub is coded within the crypter.
There are ways to detach the stub from the crypter, but in some other tutorial.
Runtime Crypters : The crypters that crypts a server that remains Undetectable upon running in the memory of a PC is called a runtime crypter.
This is the one you want for all your servers and executables.
Scantime Crypter : The crypters that crypts a server that remains Undetectable upon scanning by AntiViruses but when run in the PC gets detected by the AntiVirus.
How long my Crypter will be FUD?
Well If you have read this far chances are you still are/or will be using public crypters for a while. So chances are that your crypter will go Semi-FUD within 1-3 weeks. Depends on the crypter and your own good will.
If you want that your FUD public/private crypters to remain FUD use only novirusthanks.org with option enabled DO NOT Re-Distribute data.
Screen shot of the CORRECT way :
Well If you have read this far chances are you still are/or will be using public crypters for a while. So chances are that your crypter will go Semi-FUD within 1-3 weeks. Depends on the crypter and your own good will.
If you want that your FUD public/private crypters to remain FUD use only novirusthanks.org with option enabled DO NOT Re-Distribute data.
Screen shot of the CORRECT way :
Read more: http://thefuturehackers.com/2011/11/fud-cryptors-complete-tutorial.html#ixzz1iyA6UnpW
CopyRights: Please Stop Stealing contents from our site i.e xedlgubaid.blogspot.com . I am working hard to create an article, you simply copying? Please respect our hard work. Atleast place backlink to our site & give credit to our blog/author. Hope you will understand our feelings.


http://www.behindthefirewalls.com/2013/09/how-to-bypass-antivirus-using-veil-on.html
ReplyDeleteHelloo mate great blog
ReplyDelete